Prevent SAP Risks with Custom Code Vulnerability Analysis
Introduction
Custom code in SAP systems is both a blessing and a curse. It helps businesses tailor their processes but also introduces vulnerabilities, technical debt, and compliance risks. That’s where Custom Code Vulnerability Analysis comes in—helping organizations detect and mitigate risks while ensuring long-term maintainability.
In this article, we’ll explore the key pain points of custom code, the importance of vulnerability analysis, and how KTern.AI’s advanced KPIs make the process more efficient and reliable.
Why Custom Code Vulnerability Analysis Matters
Let’s be real—custom code isn't going anywhere. Organizations rely on it to adapt SAP systems to their unique business needs. But over time, legacy code accumulates, security vulnerabilities creep in, and businesses struggle with the following challenges:
- Security Risks – Hard-coded credentials, directory traversal vulnerabilities, and dynamic SQL statements expose businesses to cyber threats.
- Poor Code Quality – Legacy ABAP code may contain syntax errors, performance bottlenecks, and unoptimized logic.
- Lack of Visibility – Without an automated tool, it’s tough to track vulnerabilities across thousands of lines of code.
- Compliance Concerns – Regulations like GDPR and SOX demand robust security measures, making vulnerability analysis crucial.
To address these pain points, businesses need a structured way to analyze custom code, identify risks, and take proactive steps toward remediation.
Key KPIs in Custom Code Vulnerability Analysis (Powered by KTern.AI)
KTern.AI’s Custom Code Vulnerability Analysis offers a data-driven approach, breaking down vulnerabilities with well-defined KPIs that provide actionable insights. Let’s dive into these KPIs and understand their real-world impact.
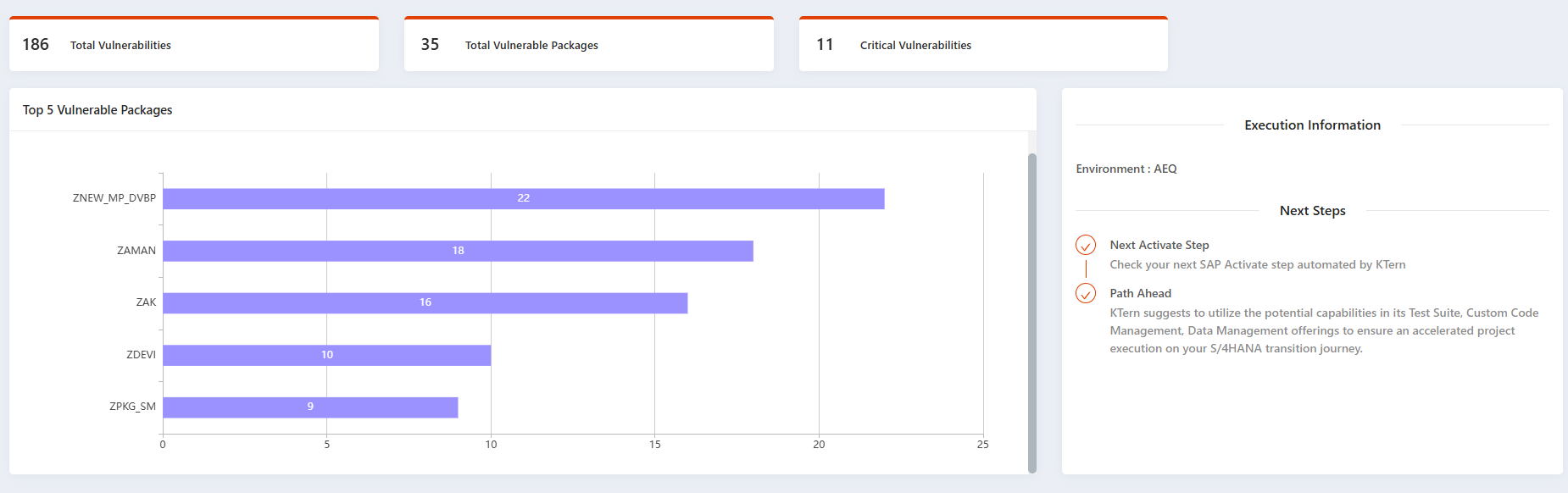
1. Security Risk Assessment
Security should never be an afterthought. This KPI highlights potential security gaps within custom ABAP code:
- Identification of Hard-Coded User Credentials – Avoids unauthorized access by flagging static usernames and passwords in source code.
- Detection of Directory Traversal Vulnerabilities – Ensures that malicious actors cannot exploit path manipulation vulnerabilities.
- Dynamic Procedure Calls in ABAP – Detects unsafe dynamic calls that could lead to code injection risks.
Value Added: Helps organizations strengthen their SAP security posture and prevent data breaches before they happen.
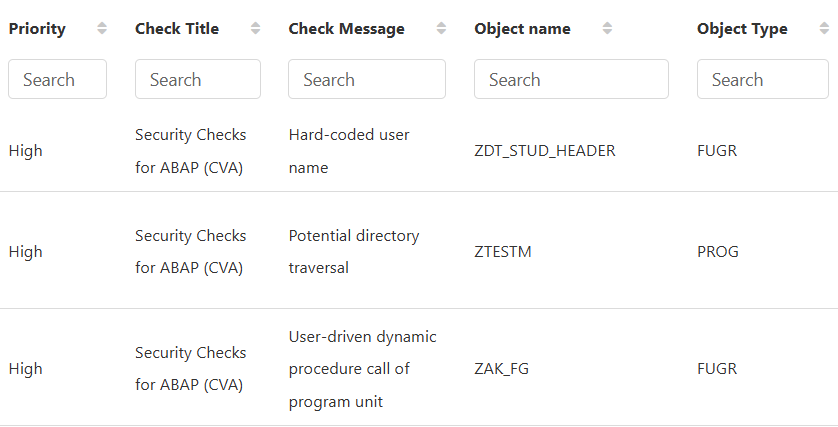
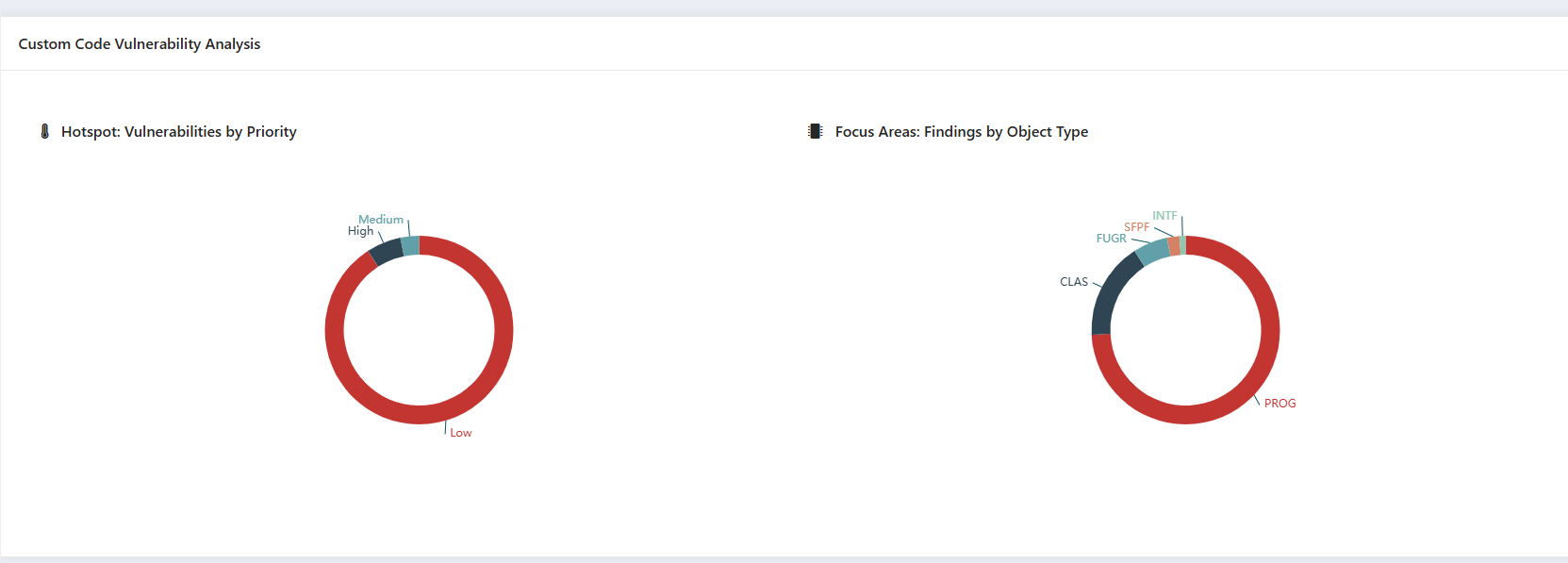
2. Object-Specific Analysis
Organizations often struggle to pinpoint which parts of their code need attention. This KPI provides:
- Categorization by Object Type (Program, Function Module, Class, etc.) – Helps teams prioritize issues efficiently.
- Tracking of Code Changes by User & Developer – Enhances accountability and change management.
Value Added: Provides better visibility into code complexity and ownership, ensuring effective remediation strategies.
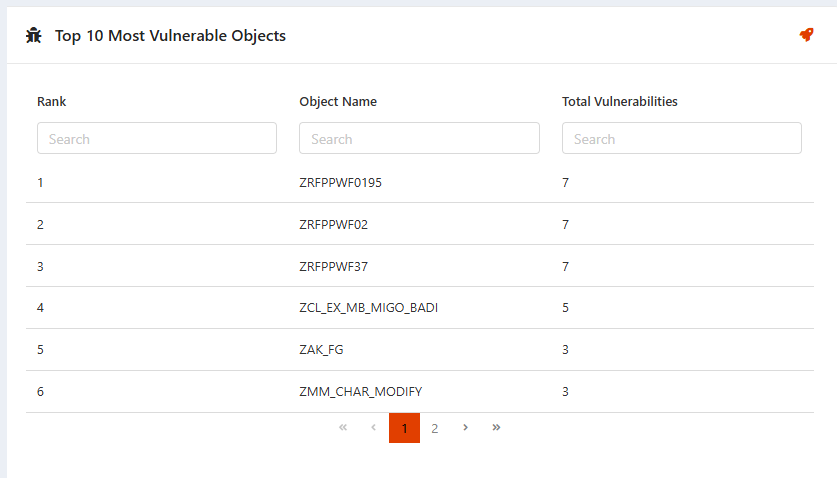
3. Exemption & Compliance Status
Sometimes, not all vulnerabilities require immediate fixes. This KPI allows:
- Exemption Tagging for Specific Vulnerabilities – Ensures that valid exceptions are documented for audit purposes.
- Assignment of Responsible Contacts for Resolution – Improves collaboration by assigning owners to remediation tasks.
Value Added: Streamlines compliance reporting and ensures security risks are effectively managed without unnecessary noise.
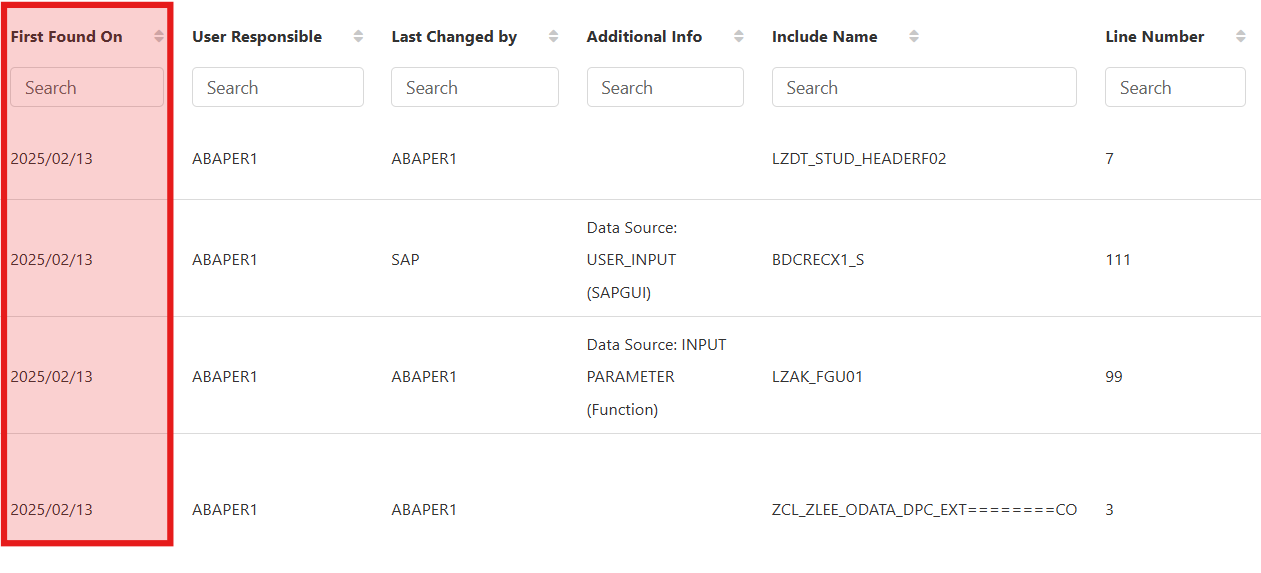
4. Timestamped Issue Tracking
Monitoring the evolution of vulnerabilities is crucial for long-term improvement. This KPI provides:
- First Occurrence & Latest Detected Timestamping – Tracks the historical presence of issues.
- Trend Analysis for Vulnerability Growth – Helps assess whether security risks are increasing or decreasing over time.
Value Added: Helps organizations measure progress in security improvements and avoid recurring vulnerabilities.
The Business Impact of Custom Code Vulnerability Analysis
Now that we understand the KPIs, let’s look at the business benefits of proactive vulnerability analysis.
- Reduced Security Risks – Early identification of security loopholes prevents cyber threats and ensures data integrity.
- Lower Technical Debt – Eliminating redundant, poorly written code improves system maintainability and reduces operational overhead.
- Improved Compliance – Organizations can meet regulatory requirements with documented risk assessments and exemption handling.
- Optimized Development Cycles – Fixing issues early in the development process reduces costly rework and deployment failures.
With KTern.AI’s automated approach, businesses no longer have to rely on manual code reviews or patchwork security solutions. The platform integrates seamlessly into SAP environments, providing real-time insights and reducing the burden on development and security teams.
Conclusion: Future-Proofing SAP Custom Code
Custom Code Vulnerability Analysis isn’t just a security measure—it’s a strategic investment. With KTern.AI’s robust KPIs, businesses can take a proactive approach to security, compliance, and performance optimization.
The key takeaway? Don’t wait for a security breach or system failure to fix vulnerabilities. By leveraging automated analysis, tracking KPIs, and ensuring accountability, organizations can maintain a secure and efficient SAP landscape.
Ready to take control of your custom code security? Start your vulnerability analysis today with KTern.AI. Contact Us Now




